
In today’s hyper-connected digital landscape, managing user identities securely and efficiently is no longer optional—it’s a strategic necessity. Identity Life Cycle Management (ILM) lies at the heart of modern identity governance, enabling organizations to ensure the right people have the right access at the right time—and for the right reasons.
At intiGrow, we help enterprises build, streamline, and future-proof their identity programs with end-to-end ILM strategies that balance security, compliance, and productivity.
What is Identity Life Cycle Management?
Identity Life Cycle Management (ILM) refers to the end-to-end process of managing user identities throughout their journey within an organization. From initial onboarding and access provisioning to changes in roles and final deprovisioning, ILM ensures that identities are tracked, rights are correctly assigned, and access is revoked when no longer needed.
Why ILM Matters in Identity Governance and Administration (IGA)
A well-executed ILM process enhances an organization’s security posture, strengthens regulatory compliance, and streamlines operations by:
o Ensuring governance policies are consistently enforced
o Automating high-volume identity tasks
o Enabling smooth onboarding/offboarding for employees, contractors, and partners
o Offering scalable solutions to accommodate cloud and hybrid IT environments
Core Components of a Modern ILM Program
Here are the foundational elements of a best-in-class ILM strategy:
✅ 1. Proper Data Management
Ensuring accurate and secure handling of identity data is critical. Identity information must be consistent across all integrated systems to avoid security blind spots or duplicate accounts.
👤 2. Centralized Provisioning and Deprovisioning
Automate user creation, modification, and deletion from a unified dashboard to minimize manual errors and speed up onboarding/offboarding.
🔄 3. Identity Synchronization
Ensure identities are synced across on-prem and cloud environments for seamless access control and data integrity across systems.
📜 4. Governance and Standardization
Establish robust access control policies, enforce least-privilege principles, and maintain consistency in how identities are managed across departments.
🤝 5. Contractor Management
Require legal agreements before granting access to external contractors. Apply time-bound access rules (e.g., 3-month limits) to maintain security and meet audit requirements.
📑 6. Documented IGA Policy
Codify your governance policies in a written IGA framework. This prevents ad hoc decisions, supports regulatory compliance, and reduces policy ambiguity.
🧠 7. Leveraging AI for ILM
Use GenAI-powered assistants embedded in familiar tools like Microsoft Teams to provide real-time, context-aware insights. AI can reduce decision-making friction and enhance user understanding across identity processes.
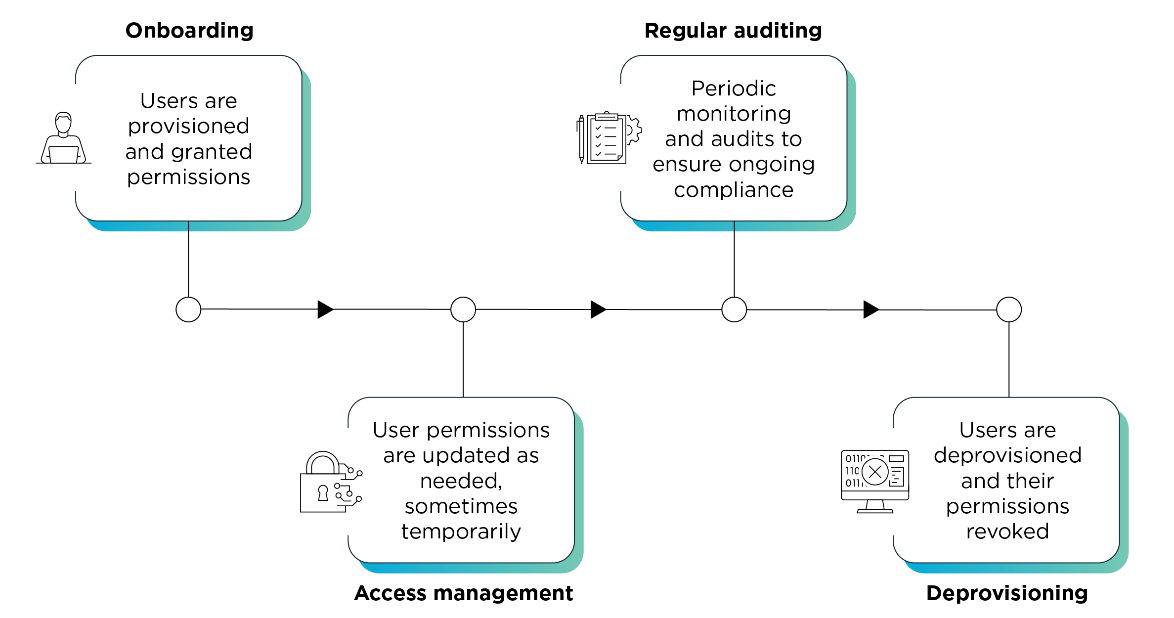
The ILM Lifecycle in Action
Here’s how a typical identity lifecycle unfolds within a secure ILM solution:
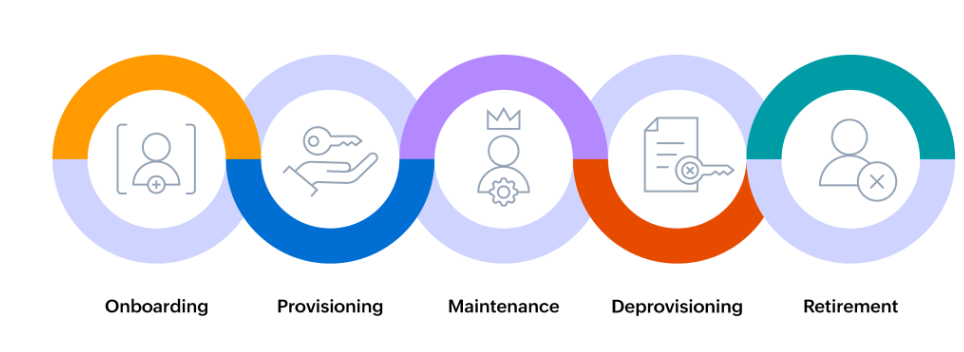
- Onboarding
Accounts are created based on job roles with predefined access privileges. Initial identity verification is conducted.
- Access Management
Roles evolve over time—ILM updates access rights dynamically. Temporary privileges can be granted for time-bound projects.
- Regular Auditing
Activities and permissions are continuously monitored and logged. Audit trails help maintain compliance with standards like GDPR, HIPAA, or SOX.
- Deprovisioning
When users leave or change roles, their access is revoked instantly across all systems to prevent lingering security risks.
ILM in Cloud and Hybrid Environments
Modern ILM must span both cloud and on-premises infrastructures. A hybrid ILM approach allows organizations to:
o Manage growing numbers of user identities across distributed systems
o Maintain visibility and control regardless of where data or applications reside
o Integrate seamlessly with third-party identity providers, SIEM tools, and directory services
Real-World Benefits of ILM
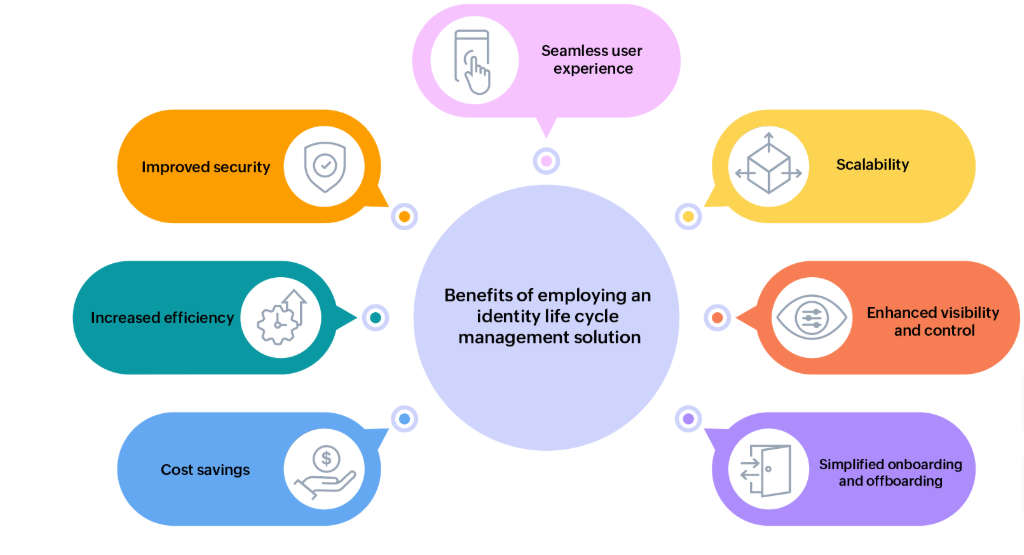
Organizations that implement ILM effectively experience tangible advantages:
Reduced Security Risks: Eliminates orphan accounts and privilege creep
Improved Compliance: Ensures policy enforcement and complete audit trails
Operational Efficiency: Automates repetitive tasks, lowering IT overhead
Enhanced User Experience: Speeds up access, improves onboarding, and supports self-service
Scalability: Facilitates secure growth and supports remote or third-party users
Your Trusted Partner in Identity Management
At intiGrow, we bring over two decades of cybersecurity expertise to help organizations design, implement, and optimize their identity life cycle management programs. From policy development to automation and AI integration, we enable businesses to secure access, simplify compliance, and scale confidently in a digital-first world.
Ready to Streamline Your Identity Lifecycle?
Let us help you build a modern ILM strategy tailored to your organization’s needs.
👉 Contact us today to schedule a consultation with an intiGrow identity expert.



