In today’s digital age, enterprises must prioritize security in order to protect their assets and data. One approach that has proven effective in protecting against cyber threats is the Zero Trust model.

Here are 10 reasons why enterprises need Zero Trust security:
- Perimeter-based security is no longer sufficient in the evolving enterprise. As resources become more distributed and hybrid, traditional security measures that rely on a strong perimeter are no longer effective.
- In the cloud, data centers require shared security responsibility between the enterprise and the provider. A Zero Trust approach ensures that all actors and devices are authenticated and authorized before access is granted.
- Third-party SaaS and PaaS applications can’t be trusted blindly. It’s important to carefully evaluate these applications and implement appropriate security measures to protect against threats.
- The internet network is an unsecured network, making it important to adopt a Zero Trust approach to ensure the security of data and resources.
- In the expanding workforce, not everyone should have all-access to resources. Zero Trust principles allow organizations to enforce strict access controls and monitor activity to protect against threats.
- It is not possible to verify the security status of all WFH environments. A Zero Trust approach allows for secure access to resources from any location, ensuring the security of remote workforces.
- BYOD (bring your own device) is not as secure as work devices.
Implementing a Zero Trust model
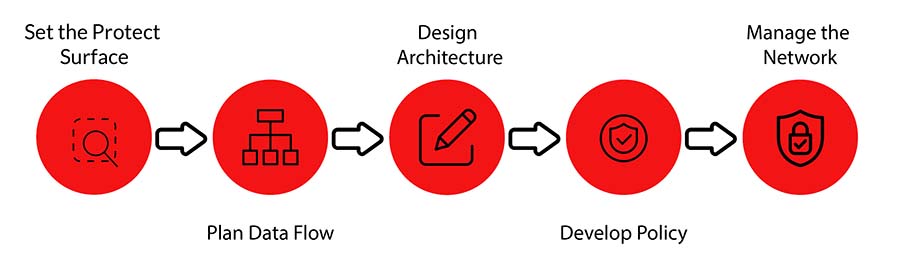
To effectively implement a Zero Trust model, it is important to prioritize the protection of your data. Here are some key recommendations for how to do this.
- Identify sensitive data: Determine where your sensitive data is located, such as internal departmental folders or storage areas for personally identifiable information (PII) or protected health information (PHI). It is important to know where your sensitive data is located and who has access to it before implementing appropriate protection measures.
- Limit access: Once you have identified your sensitive data, make sure that only those who need access to it have it. This will help to reduce the exposure of sensitive data and make it more difficult for hackers to gain access. You should audit access permissions at the individual, group, and organizational levels to ensure that only authorized users have access to sensitive data.
- Detect threats: To ensure the security of your data, you should continuously monitor and log all activity related to data access, including activity in the active directory, file and share access, and network perimeter telemetry. By comparing current activity to baselines of previous behavior and applying security analytics and rules, you can detect abnormal activity that may indicate cybersecurity threats from internal or external sources.
Benefits of Zero Trust
The adoption of a Zero Trust approach can bring several benefits to your organization. These include:
- Improved network and system visibility: By implementing Zero Trust and monitoring all data and computing sources, you can gain a deeper understanding of system activity. Every access request, including time, location, and application involvement, can be tracked and flagged for suspicious activity.
- Enhanced security for remote work: As more and more employees work remotely, traditional security measures may not be sufficient to protect critical data. Zero Trust ensures the security of distributed workforces by attaching identity to users, devices, and applications seeking access, regardless of location.
- Efficient compliance: Zero Trust helps maintain compliance with various regulatory frameworks by providing a transparent audit trail for all access requests. This simplifies the process of producing evidence for audits, making governance operations more efficient.
Limitations of Zero Trust
While Zero Trust can be a valuable tool in cyber defense, it has some limitations to be aware of when implementing it. These include:
- Managing bring-your-own-device (BYOD) policies and environments: In a BYOD workplace, the variety of devices, their properties, and communication protocols can make it more challenging to configure Zero Trust security measures.
- Handling a high number of applications: If your organization uses a large number of communication and collaboration apps, it can be difficult to implement Zero Trust for all of them. Carefully evaluate third-party data handling, storage, and the necessity of each application before adding it to your tech stack.
- Inability to determine user intentions: Even if users are fully authenticated, Zero Trust cannot determine their intentions. Malicious insiders or users with malicious intentions may still be able to compromise data or systems they are authorized to access.
In summary, the Zero Trust framework is an important consideration in today’s cybersecurity landscape, with its focus on remote work, bring-your-own-device (BYOD) policies, and the internet of things (IoT). By taking a data-centric approach to security and understanding where sensitive data exists, who can access it, and how it is being used, organizations can better defend against sophisticated threats. The adoption of Zero Trust can help limit the impact of a potential cyberattack and support compliance with cybersecurity standards.




